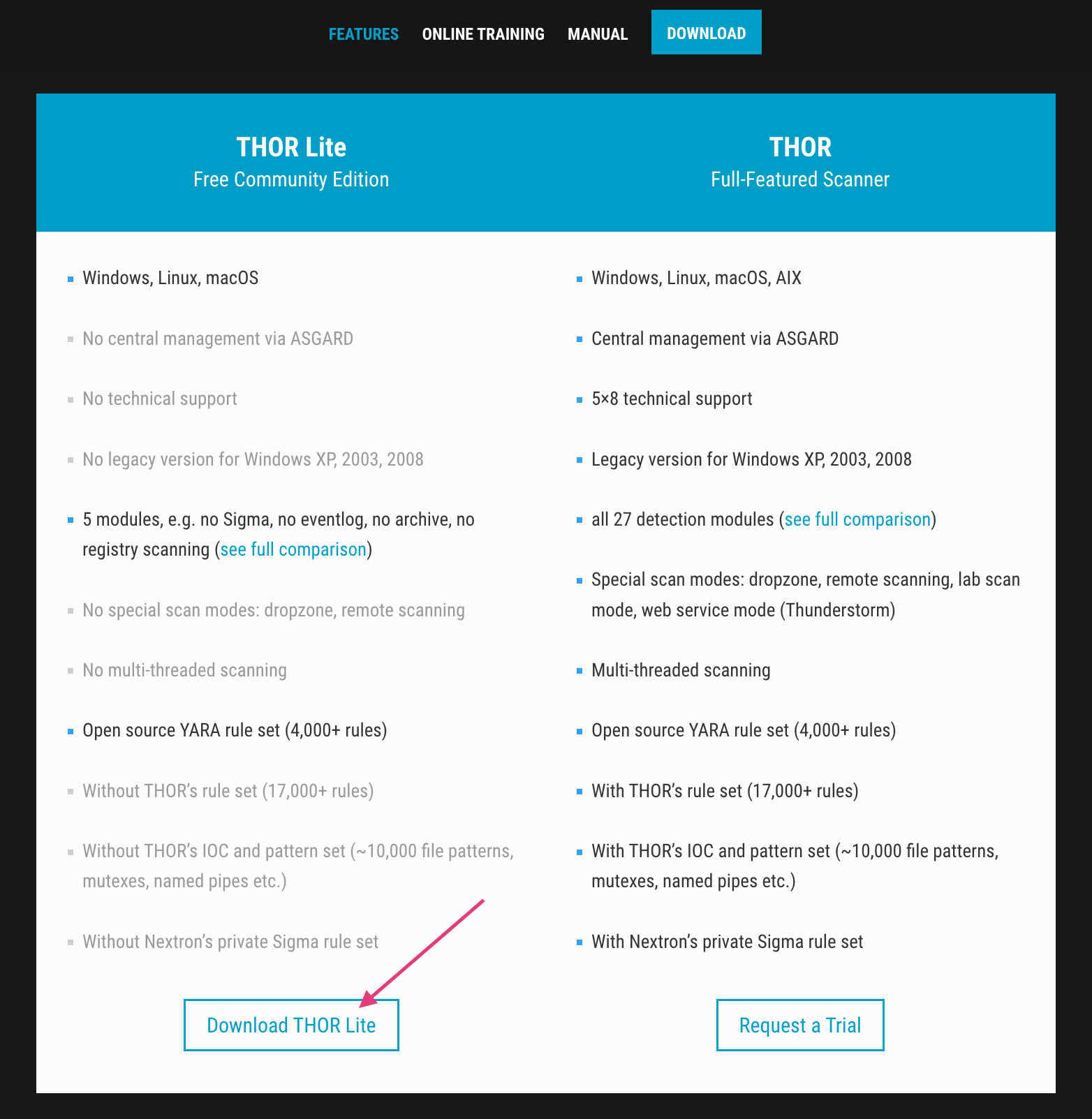
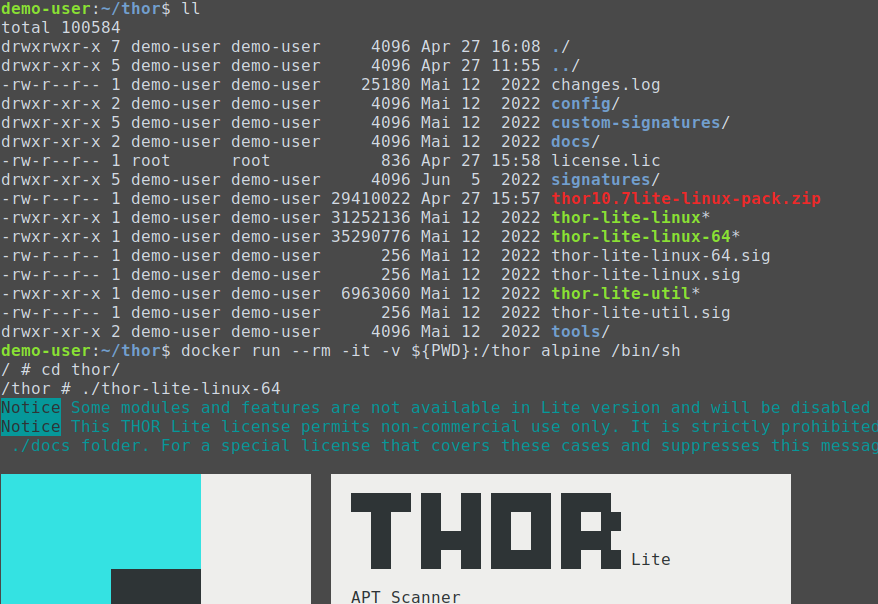
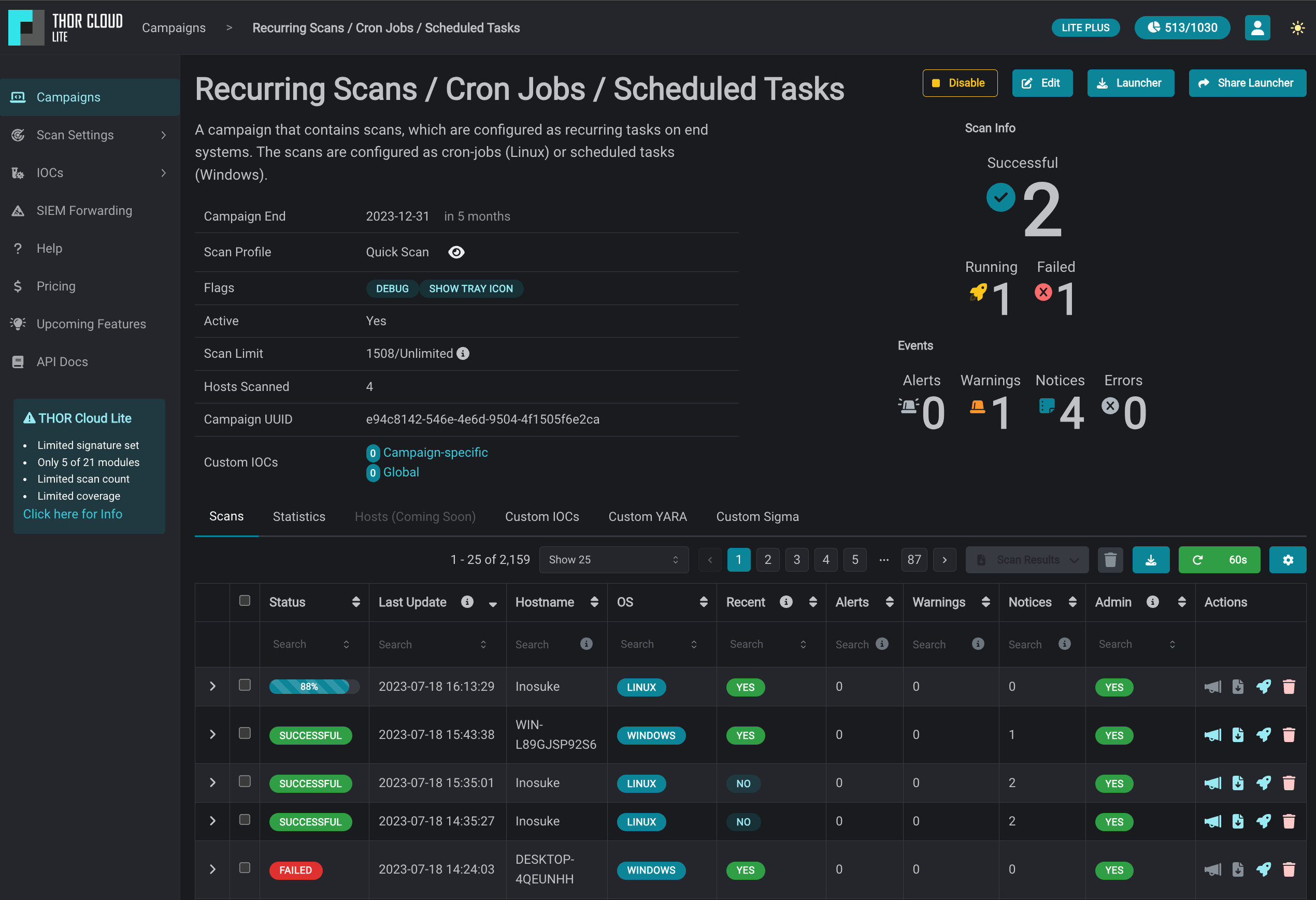
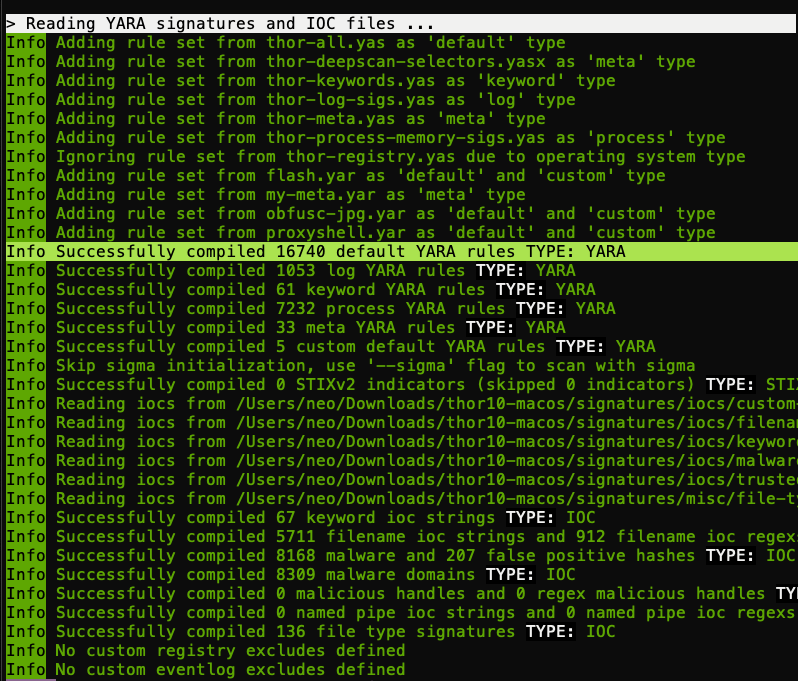
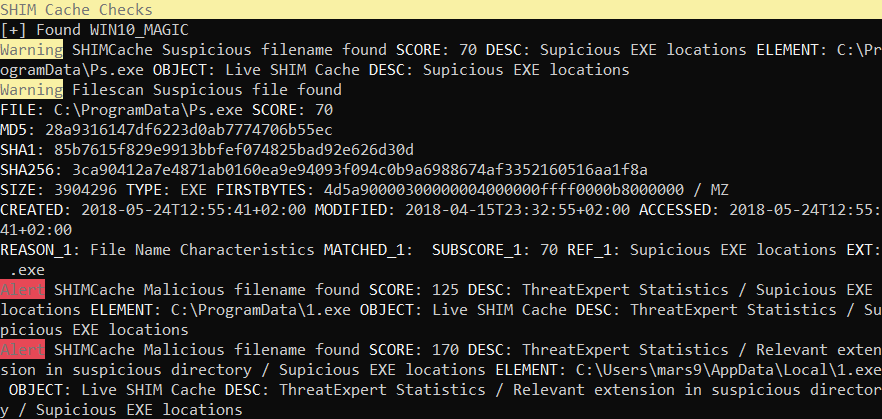
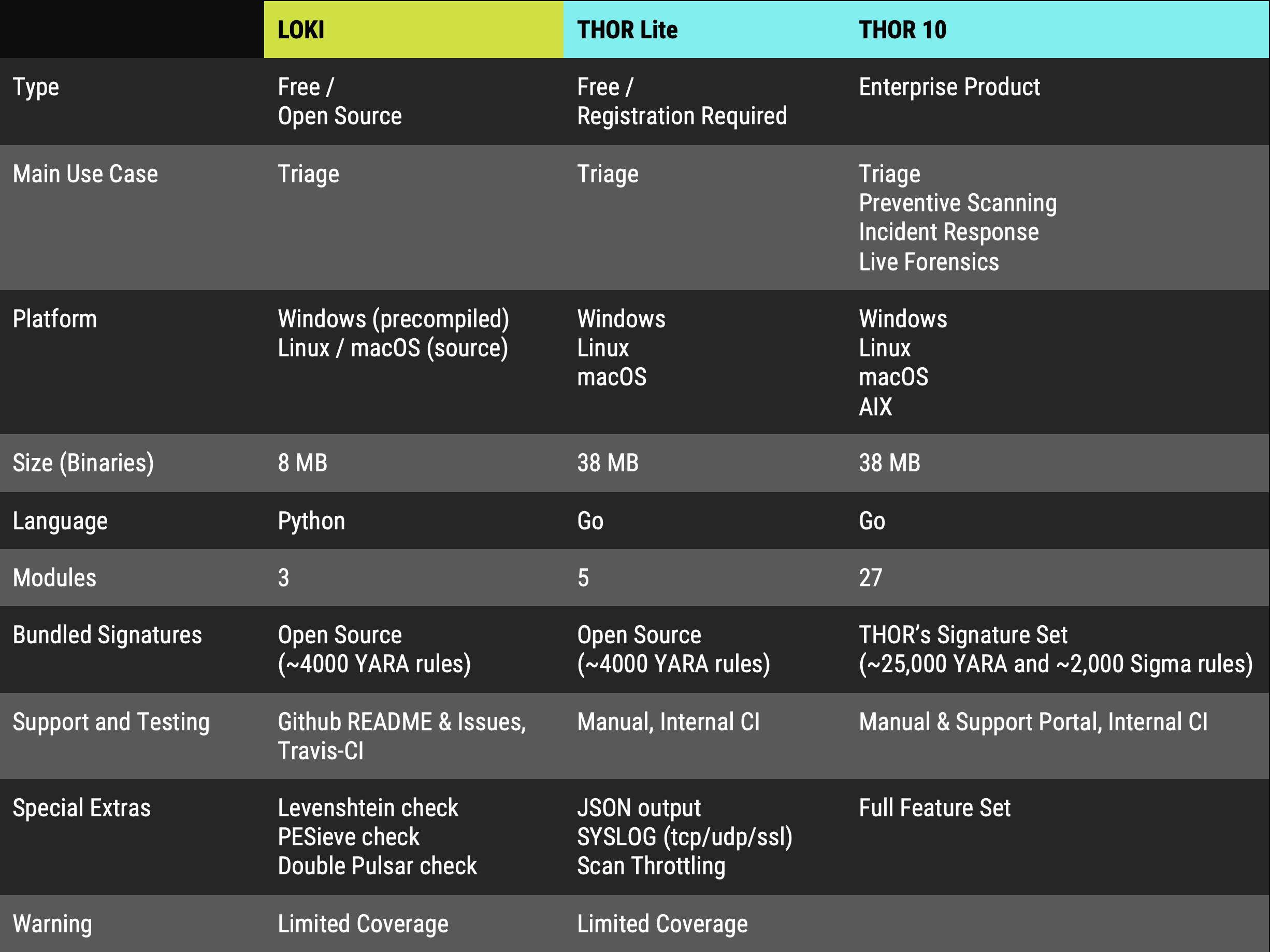
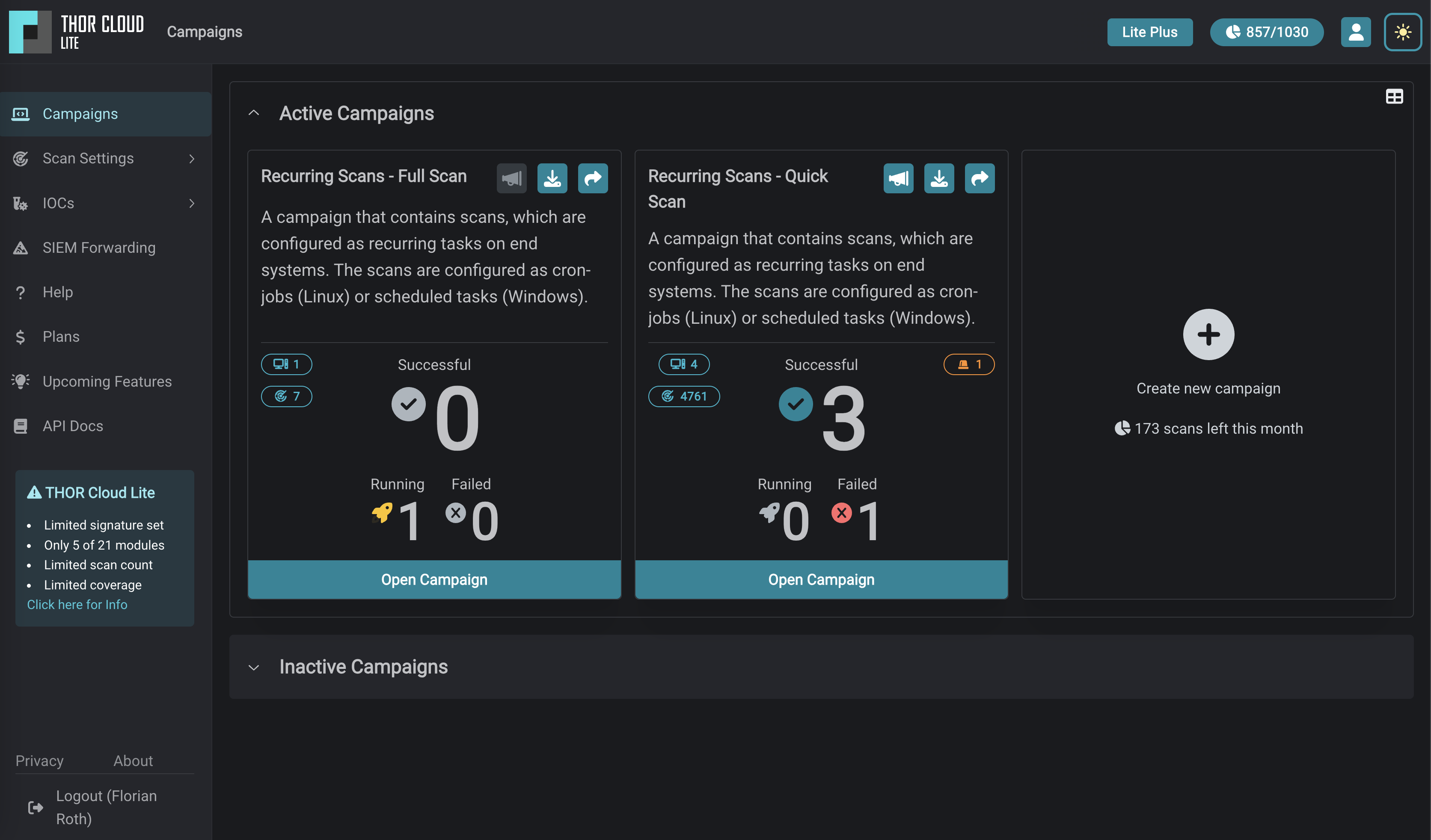
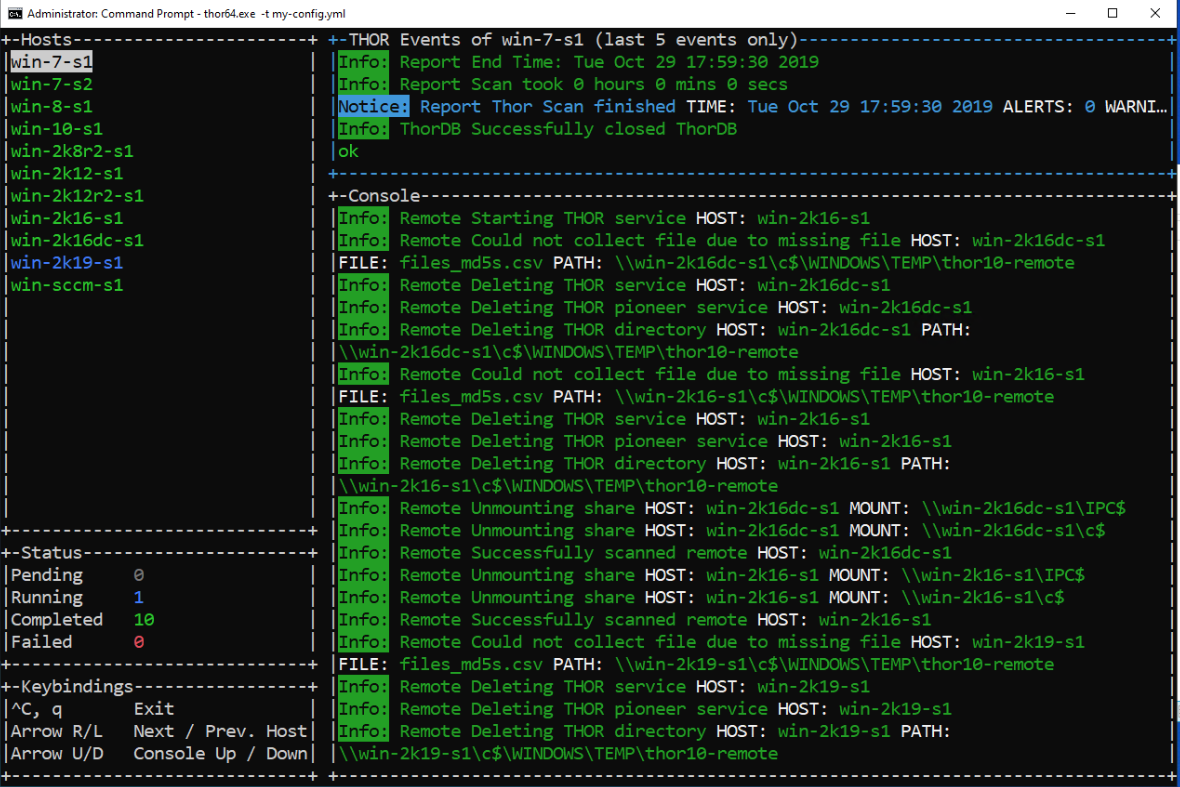
Using THOR Lite to scan for indicators of Lazarus activity related to the 3CX compromise - Nextron Systems

How to scan systems with THOR lite scanner during compromise assessment and incident response | by Md. Mahim Bin Firoj | Medium
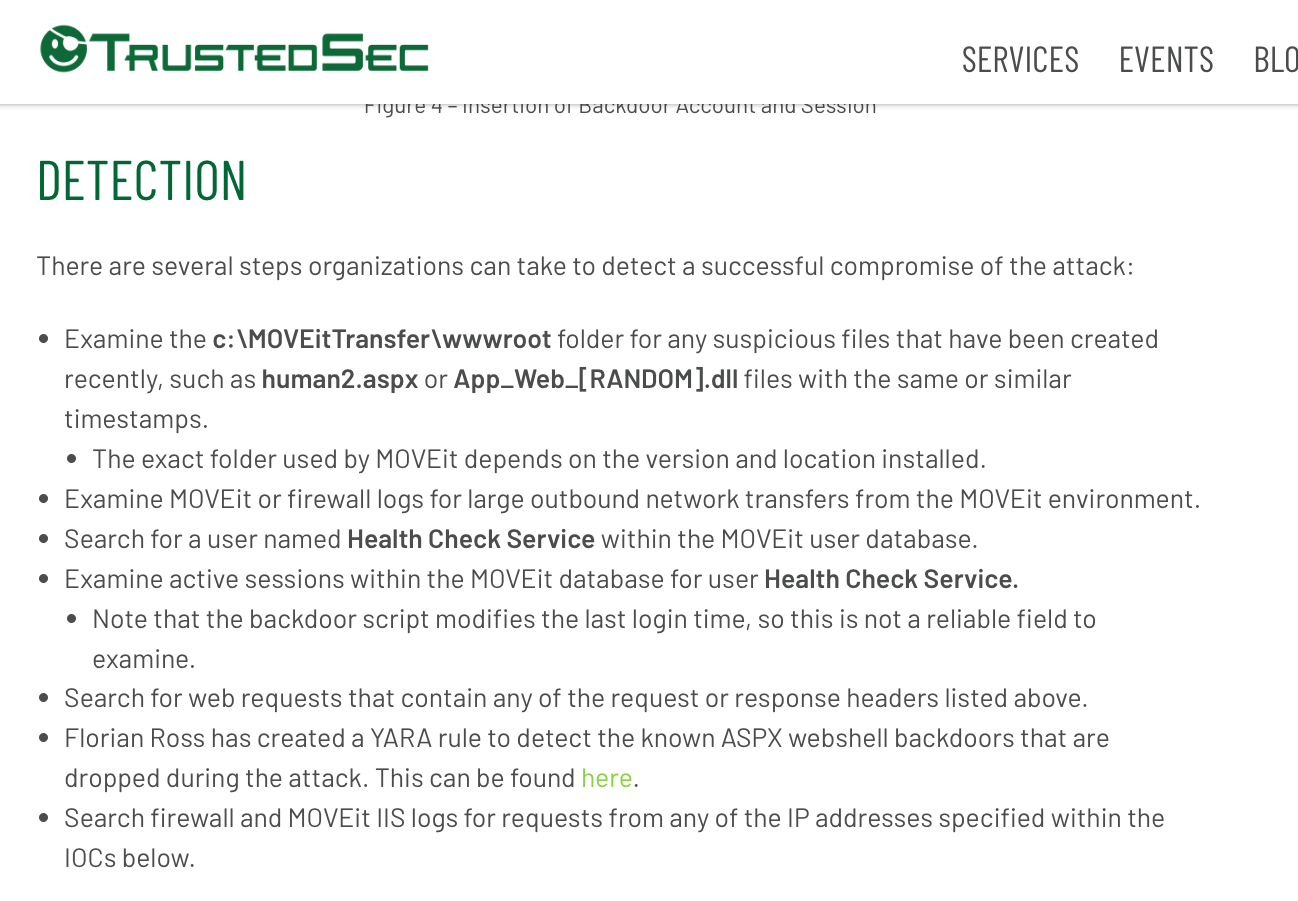
Using THOR Lite to scan for indicators of Lazarus activity related to the 3CX compromise - Nextron Systems
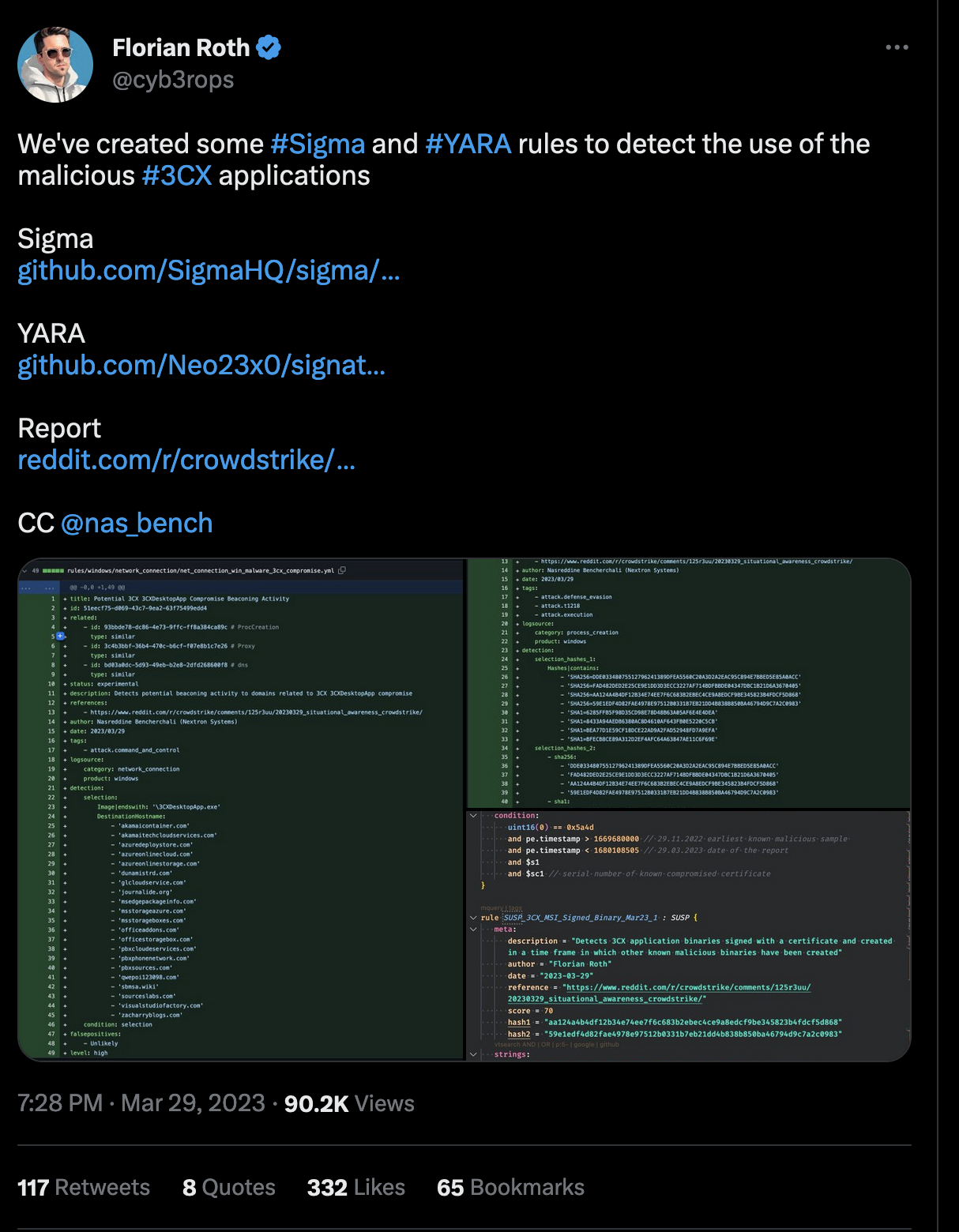
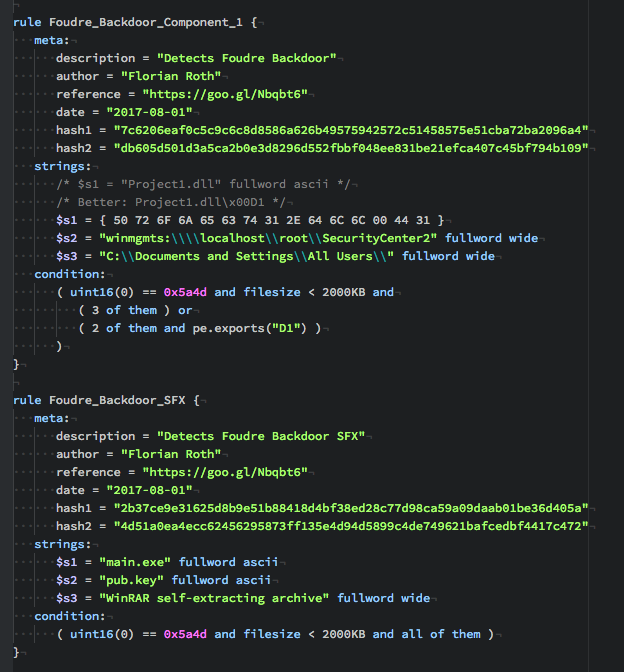
Using THOR Lite to scan for indicators of Lazarus activity related to the 3CX compromise - Nextron Systems