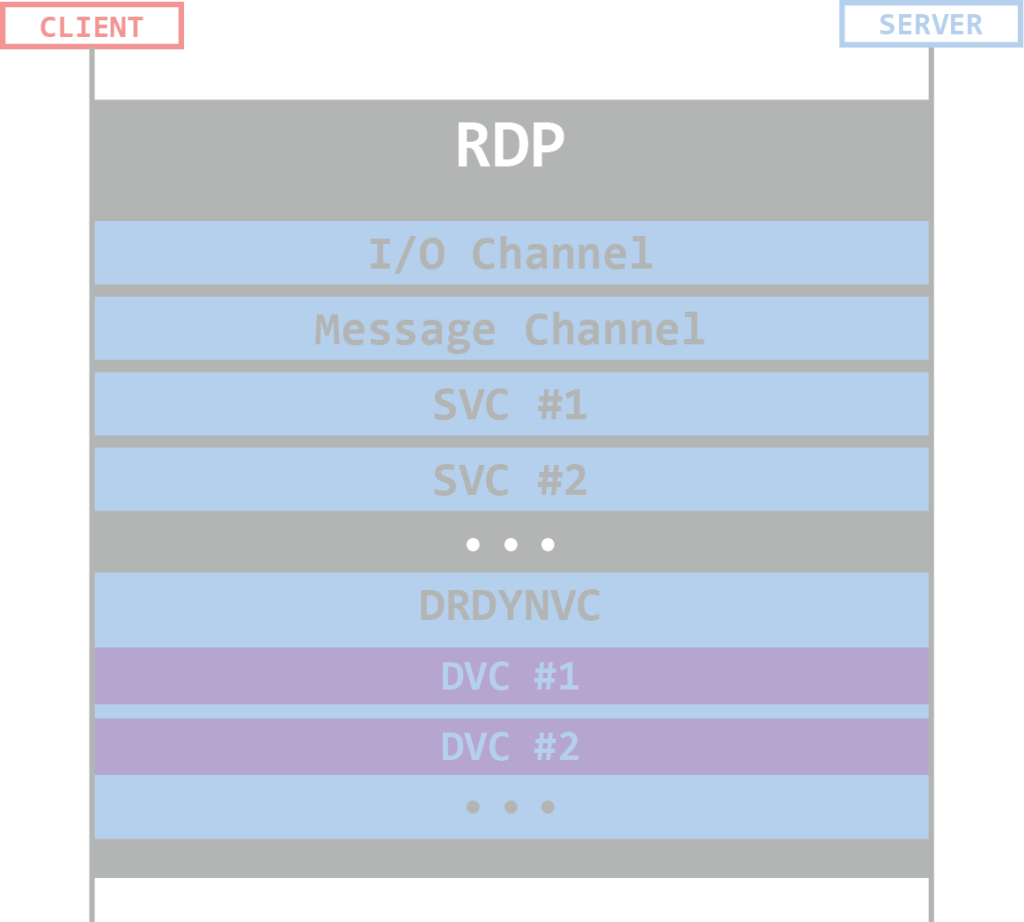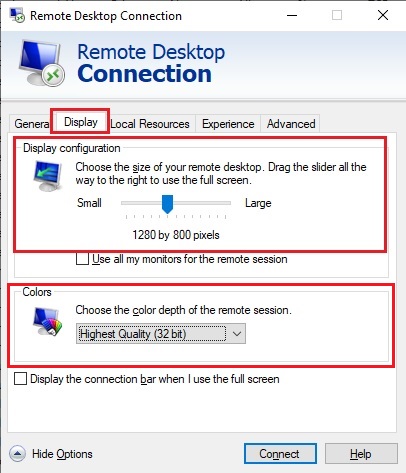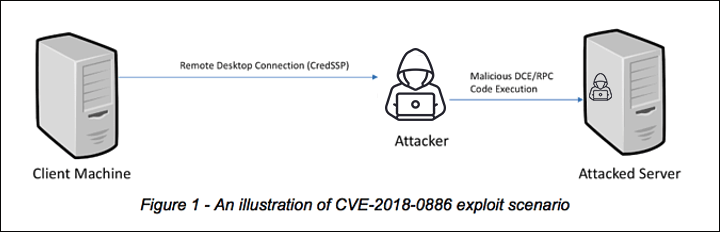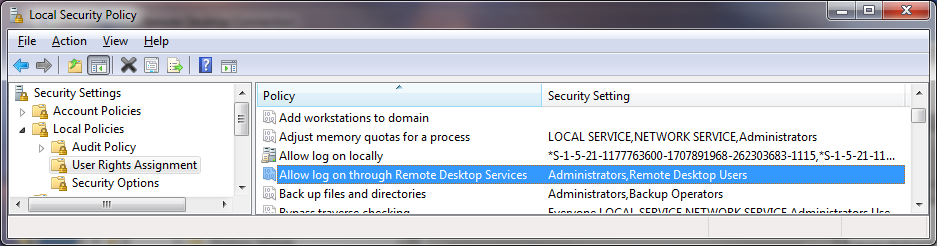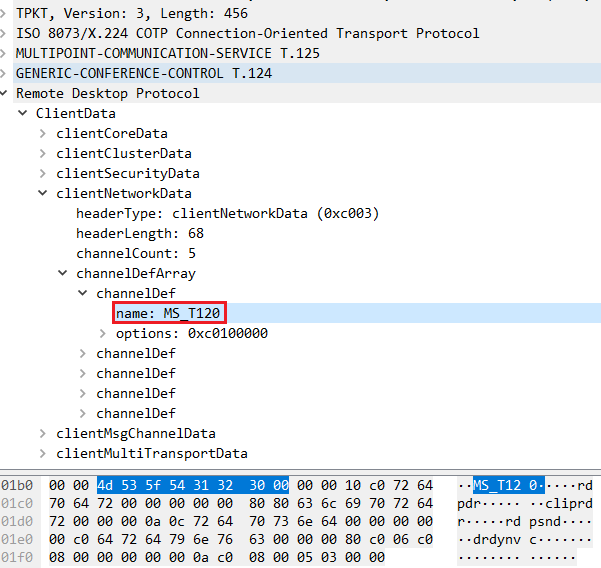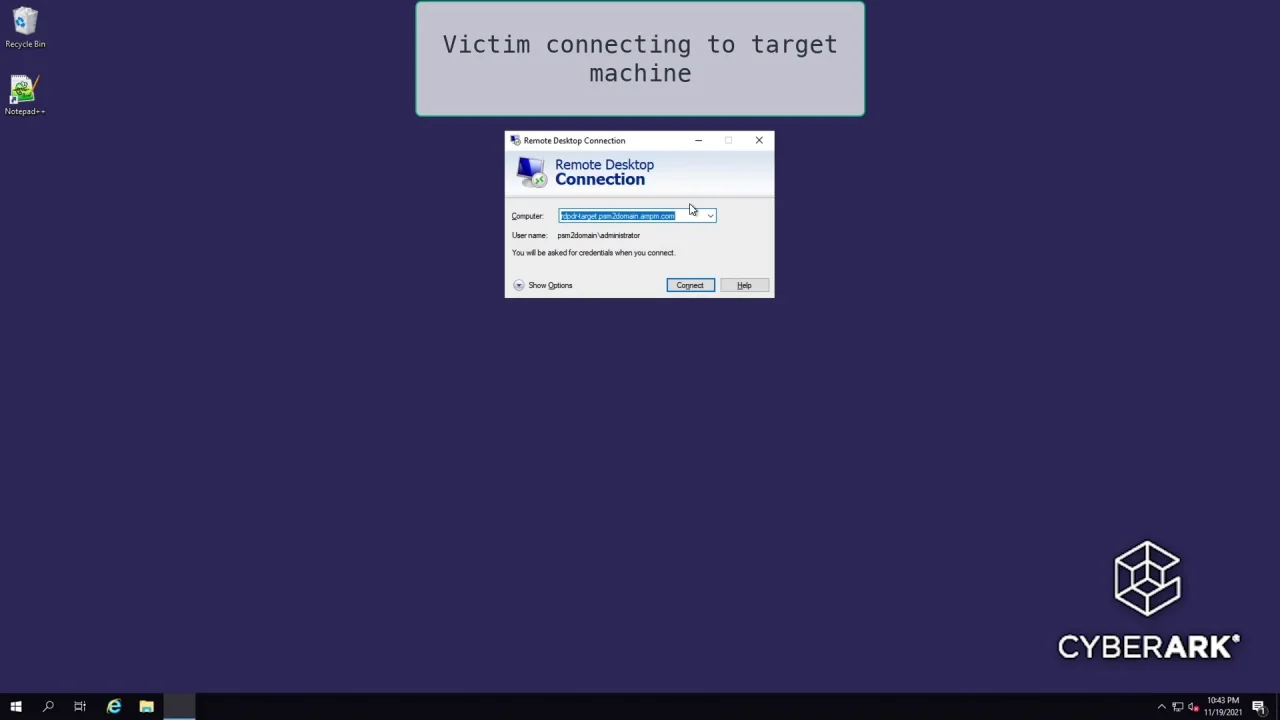
Attacking RDP from Inside: How we abused named pipes for smart-card hijacking, unauthorized file sys

Attack Chain Series: Remote Access Service Compromise Part 1 — RDS | by Vartai Security | Vartai Security | Medium

Attack Chain Series: Remote Access Service Compromise Part 1 — RDS | by Vartai Security | Vartai Security | Medium